

Being secure must be considered as essential rather than optional. Our company provides exceptional security protection.
We provide full security solutions to defend your business and offer security consulting and network security services.
Our VAPT services use detailed tests and relevant information to help you build stronger infrastructure systems.
Our web security solutions provide end-to-end protection, ensuring data integrity and user trust.
Your website needs protection against cyber threats as well as malware defense together with DDoS attack prevention.
Protect all communication pathways through encryption while using threat detection functions.

Trust us to keep your business safe with cutting-edge encryption, proactive monitoring, and robust defense strategies.
We deliver premium security technology that protects your website from any virus. Protecting our clients through innovative security measures produces reliable platforms based on trust, which deliver flawless solutions that build digital strength for business success in protected online spaces.


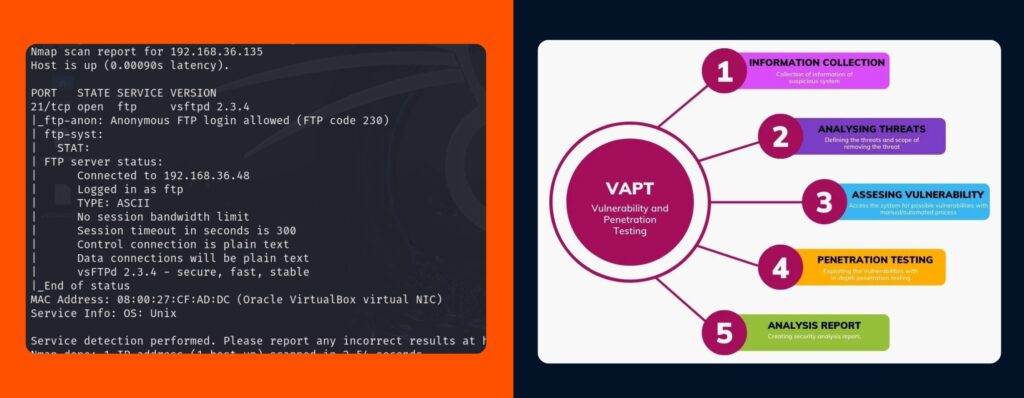
We provide huge Vulnerability Assessment and Penetration Testing (VAPT) offerings to pick out security flaws earlier than attackers take advantage of them. Our services assist businesses in strengthening their protection posture and safeguarding sensitive information.
Steps to Implement VAPT
Step 1: Evaluation and Scoping: Identify potential security risks.
Step 2: Testing: To identify weaknesses, run an automatic scan.
Step 3: Analysis and utilization: Model real attacks to assess the safety of a system.
Step 4: Treatment and reporting: Provide a comprehensive report that describes the weaknesses and suggests the solution.
We offer advanced cloud firewall solutions to protect our cloud infrastructure from online threats and illegal access. On many cloud platforms, our safety protocol guarantees real-time performance, strict access control, and continuous protection.
Steps to Implement Cloud Firewall
Step 1: Policy Setup—Define safety guidelines and decide which traffic is allowed or blocked.
Step 2: Deployment & Configuration—Install the firewall on the network and set up the traffic rules.
Step 3: Detection & Monitoring—Make traffic surveillance and in-depth inspection possible.
Step 4: Maintenance & Testing—Update the firewall frequently, check the rules, and confirm the efficacy of the protection.


We offer web security solutions to protect your site from Internet dangers, hacking, and data breaches and offer secure operations for firewall, SSL encryption, DDOS defense, ongoing monitoring, and danger identification.
Steps to Implement Web Security
Step 1: Risk assessment and basic security: Use the Web App Firewall (WAF) and consider the hazards of the site.
Step 2: Secure communication and access: Enable SSL/TLS (HTTPS) and resident strong user authentication (MFA).
Step 3: Continuous monitoring and prevention of danger: Install DDOS security, monitor traffic, and search for flaws.
Step 4: Maintenance and test: Perform safety audits and recording tests, and update the software and plugins regularly.
Our Mail Security solutions include domain authentication, encryption, real-time threat detection, and sophisticated filters to protect against viruses, spam, and phishing.
Steps to Implement Mail Security
Step 1: Email approval and access control: Configure e-mail accounts with DMARC, DKIM, SPF, and MFA.
Step 2: Spam filtration and encryption: Place the anti-phishing/spam filter in place and scan the email from beginning to end.
Step 3: Awareness and monitoring: Keep an eye on suspicious activity and give employees e-mail safety training.
Step 4: Backup and revision: Regular backup and security audit to ensure data retention and protection.

Get free expert advice, customized to your needs.
Innovative solutions, seamless connectivity, and expert support!
Threats that may damage sensitive data and interfere with operations include ransomware, phishing, DDoS, data breaches, and insider threats.
Use strong password policies, enable multi factor authentication (MFA), serve regular security audits, train employees on best cyber security practice and distribute advanced firewall and endpoint protection.
To prevent such attacks, reset all credentials, alert the relevant parties, isolate the compromised computers immediately, scan for dangerous software, restore data from a secure backup, and conduct a forensic investigation.
Vulnerability Assessment and Penetration Testing (VAPT) helps identify security loopholes before attackers do, allowing businesses to fix weaknesses and strengthen their defense systems. Vulnerability Assessment and Penetration Testing (VAPT) helps businesses identify security issues before attackers do, allowing them to strengthen their defenses and remedy vulnerabilities.
A Zero Trust strategy guarantees that each device has been verified before gaining access to the network or being removed from it. This strict security approach requires identity verification, least privilege access, and continuous threat monitoring.
Encrypt important data, activate Identity and Access Management (IAM), set up security groups correctly, carry out frequent audits, and make use of AI-powered threat detection technologies.
Embtel Solutions is your one-stop destination for comprehensive solutions that drive business growth. We empower you with innovative technology, security, and digital expertise to ensure success in today’s competitive landscape.
©2025 embtelsolutions.com,Inc. All Rights Reserved.